In this section we are going to provide a Background to Content Management Systems with a look at what a Content Management System is and then go on to look at specific options for Web Content Management Systems available today. We will then discuss the subject of this report, WordPress, in more detail. Finally, we will end with a discussion of what Wordfence is, how it works and how Defiant Inc. goes about the process of disclosing vulnerabilities responsibly.
A Background to Content Management Systems – What They are and Why We Need Them
A Content Management System (CMS) is a software package that provides some level of automation for the tasks required to effectively manage content (Barker, 2016).
Modern CMS are usually multi-user, server-based applications that uses content stored in a repository of some sort, usually a database located either on the same server or a remote location. They allow editors to create new content or edit existing content, making it available for other users to access.
There are a number of different types of CMS, however the “Big 4” are:
- Web Content Management (WCM) – The management of content intended for delivery via a website.
- Enterprise Content Management (ECM) – Managing general business content that is not intended for a mass audience, for example employee CVs or incident reports.
- Digital Asset Management (DCM) – Management of digital assets like audio, video and images.
- Records Management (RM) – Managing transactional information like sales records or access logs.
This report is going to focus on Web Content Management Systems.
Web Content Management System Options
There are a number of Web Content Management Systems available – some free to use Open-Source, and some paid-for commercial options.
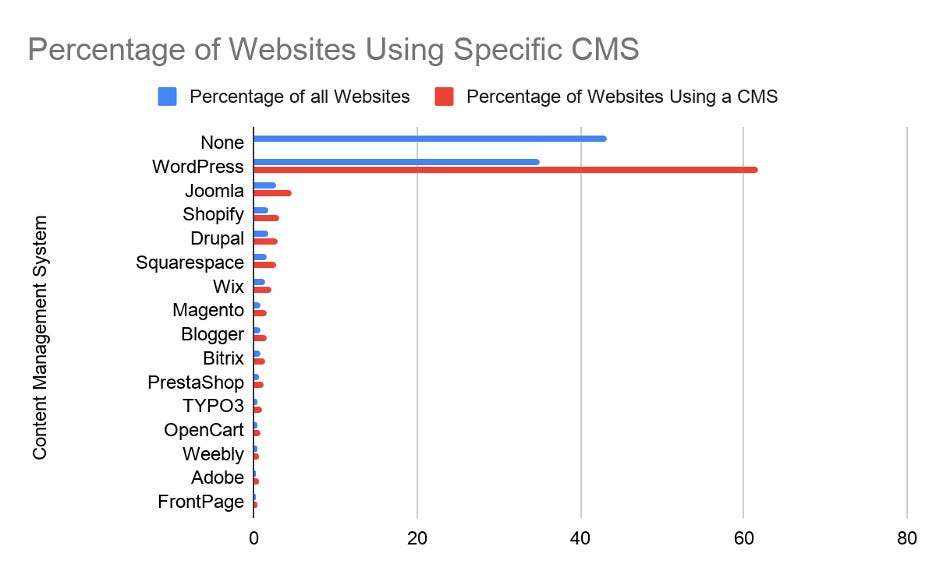
Figure 2.1 – Percentage of Websites Using a Specific Content Management System
Joomla
Joomla is a free, open-source CMS written in PHP, with either MySQL, MSSQL or PostgreSQL database backend. There are over 6000 free or paid-for extensions for Joomla that extend its functionality. It is currently listed as the second most popular CMS, with 2.7% of websites powered by Joomla globally (w3techs.com, 2019).
Joomla first appeared in 2005 as a fork of the Mambo CMS project and is developed by a core team with an active team of additional contributors
Drupal
Like most of the other top CMS, Drupal is free and Open-Source, written in PHP with support for a variety of databases. It currently powers 1.7% of all websites globally and has been an open-source project since 2001. Again, it is also supported by an active community of developer contributors.
Drupal uses a system of modules and themes to extend its functionality and allow it to be customised accordingly.
Shopify
Shopify is a proprietary e-commerce application developed by the Canadian company, Shopify Inc. It accounts for 1.8% of all websites globally and claims to have facilitated over $41.1 billion in sales globally through its platform in 2018. They also claim to have over 1,000,000 businesses on their platform in over 175 countries. They are the only commercial, non-open-source CMS in the top 4 CMS by number of sites. The founders of the company first built the application when setting up their own online snowboard equipment ecommerce site in 2004. Dissatisfied with what they found available to them off-the-shelf, they built Shopify using the open-source Ruby-on-Rails framework.
Unlike the other top CMS options, Shopify hosts customer sites on their own platform, however they do offer an API that allows developers to create and sell applications for Shopify shops.
Custom-Built Web Content Management Systems
Like the developers of Shopify, who decided to build their own CMS, there are countless numbers of custom-built CMS, developed by individual developers who decided they could do a better job themselves. There are many difficulties with this approach, particularly if the developers themselves are not the owners of the site. The owners of the site would have to maintain a permanent relationship with the developers of the site and rely on them alone for any changes or updates. There would also be little scrutiny of any bugs or security issues with the site, possibly leading to exploitable vulnerabilities. Obscurity may allow the site to stay “under the radar” and prevent attacks from hackers targeting the main CMS variants.
WordPress
This report is going to focus on the security of sites running WordPress. Current statistics show that WordPress currently powers 36% of the web, or around 61% of websites that use some form of CMS, and hackers understand economies of scale. If they develop a hack against a vulnerability in a specific WordPress component, they are going to have a potentially high number of victims, as opposed to targeting a less frequently used CMS or web component. This Figure 2.2 shows the number of attacks being blocked by WordPress sites running Wordfence over a 24-hour period.
Figure 2.2 – Total Attacks Blocked on the Wordfence Network
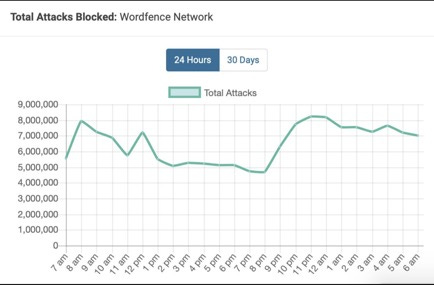
Figure 2.2 is available to view on the dashboard of a website running the Wordfence plugin and shows that WordPress sites are constantly under attack.
WordPress was first released in 2003 by its founders Matt Mullenweg and Mike Little under the GPLv2 license. (Cabot, 2018) It is famous for its quick and easy setup process, requiring just a database, with database connection details and a copy of the install files. The web-based installation takes a minute or two to run through, creating the relevant database structure and files for a working content-driven website.
Like most of the other top open-source CMS, WordPress is written in PHP with a database backend (MySQL or PostgreSQL for example) and is usually hosted on Linux-based servers. Users of WordPress include small hobbyists to large ecommerce to global news organisations.
WordPress can be extended from the base core with the use of third-party plugins and themes. Many of these are approved by WordPress and available through the WordPress repository. Others are available to download from developers, sometimes at a price. The use of unapproved, third-party plugins brings with it a range of problems that will be discussed later in the report. There are currently over 54,000 plugins available in the WordPress repository, with many thousands available from other sources.
A plugin is a script or group of scripts in PHP that extend the functionality of a WordPress site. They should seamlessly integrate into WordPress to add new features to the site.
Themes alter the display or layout of the site, but can also add functionality. Plugins add functionality, but can also add to the site’s layout.
There are plugins available for almost any task or purpose that could be required of a site. Below are a few examples of commonly used WordPress plugins:
- Contact Forms (Contact Form 7)
- Search Engine Optimization (Yoast SEO, All in One SEO, Google XML Sitemaps)
- eCommerce (WooCommerce)
- AntiSpam (Akismet)
- Backups (Updraft Plus)
- Security (Wordfence)
WordPress comes with a number of default themes, usually updated annually, and again there are thousands available to download from the WordPress repository or from other sources.
Matt Mullenweg went on to found Automattic, the company behind WordPress.com and a variety of major WordPress plugins.
Wordfence, Defiant Inc and Responsible WordPress Vulnerability Disclosure
Back in 2007, Cavusoglu, Cavusoglu, and Raghunathan wrote that “The rate of information security breaches has been increasing significantly. One of the main reasons for this increase is security vulnerabilities in software”. This is certainly still true today. In the same paper, they determined that “the characteristics of the vulnerability (vulnerability risk before and after disclosure), cost structure of the software user population, and vendor’s incentives to develop a patch determine the optimal (responsible) vulnerability disclosure. We show that, unlike some existing vulnerability disclosure mechanisms that fail to motivate the vendor to release its patch, responsible vulnerability disclosure policy always ensures the release of a patch” (Cavusoglu, Cavusoglu, & Raghunathan, 2007). The implication here is that, whatever the opinion of the analyst that discovers a vulnerability, the best course of action is always to disclose responsibly.
As mentioned previously, Giles has been working in this field for a number of years and is currently a Senior Security Analyst for a company called Defiant Inc, based in the US. The primary product created by this company is the Wordfence plugin for WordPress. The free version of the plugin has been downloaded over 100 million times and there are over 3 million active installs currently. In the last 30 days, the plugin has blocked 4,195,070,923 attacks and blacklisted 67,343 IP addresses.
The plugin contains a number of features, but primarily it acts as an endpoint firewall and malware scanner. The Threat Defence Feed arms Wordfence with the latest firewall rules, malware signatures and malicious IP addresses. These signatures are developed mostly based on malware samples discovered during the site clean process offered by the company. Customers pay a fee to have their site cleaned of infection or audited by an analyst from the Site Security Team.
WORDFENCE SCANNING
Wordfence scans can be scheduled or started manually. Scans examine all files on the website looking for malicious code, backdoors, shells that hackers have installed, known malicious URLs and known patterns of infections. The scan also examines the database, looking for malicious code or URLs in posts, pages and comments (Wordfence, 2020). Wordfence scans proceed through a set of stages, with each stage checking specific areas of the site. The checks performed are detailed below:
- Spamvertising checks to determine whether the website is being Spamvertised.
- Checks to see if spam is being generated by the website IP address.
- Check whether the website is on a domain blacklist.
- Monitor the available disk space for the site.
- Check the version of PHP in use and confirm compatibility.
- Scan the wp-admin and wp-includes directories for files that are not bundled with WordPress.
- Check that plugin, theme and WordPress core files match with the repository versions, looking for any changes.
- Scan the site files looking for signatures of known malicious files or backdoors, trojans and suspicious code.
- Scan comments, posts and file contents for known dangerous URLs and suspicious content.
- Scan for quarantined files, configuration, backup, or log files that are publicly accessible.
- Check the strength of user passwords.
- Look for out of date, abandoned, and vulnerable plugins, themes, and WordPress versions.
- Scan for administrator users that were created outside of WordPress – i.e. directly in the database.
Results are displayed in the Wordfence dashboard and emailed out as an alert if this is configured.
Depending on the size of the site and the performance of the server, a scan can take from one minute to several hours, so it is advisable to configure scheduled scans to run during quiet times. Administrators have the option of configuring different levels of scan, which include:
Limited – This is suitable for sites with only highly restricted resources available.
Standard – This includes all relevant checks needed to ensure that the typical WordPress site is safe. It is recommended for most sites.
High Sensitivity – This is mainly useful when there is a suspicion that the site has in fact been compromised. One of the options included in this level of scan is the “Scan images, binary, and other files as if they were executable”. This examines binary files like images, PDFs and other files to see if they are in fact hidden programs capable of executing code.
Custom – Administrators are able to make custom changes to the checks being performed by the scan.
There are two versions of the Wordfence plugin, the “Community” version, which is free, and the “Premium” version which is paid for on an annual license. The Malware Signatures status circle on the dashboard indicates whether the site is using the Community or Premium version of the malware signatures. When new malware signatures are released by Wordfence, they are applied to Premium customers’ sites immediately. Sites running the free, community version of Wordfence get the same signatures, but not until 30 days after they have been released to premium customers.
The four severity levels in scan results are as follows:
- Critical – Highlights problems that need to be examined immediately.
- High – This includes issues that should be examined as soon as possible, although they may not pose an immediate threat.
- Medium – Includes problems that customers should be aware of, but can be resolved at their discretion.
- Low – These issues can usually be safely ignored. The customer may want to be aware of them.
Web Application Firewall for the WordPress Content Management System
On installation of the Wordfence plugin on a website, Basic WordPress Protection is automatically activated. This is very important for any Background to Content Management System. This means that the plugin will load as a regular plugin after WordPress loads. This allows it to block many malicious requests, however some vulnerable plugins or WordPress itself may run vulnerable code before all plugins are loaded. Attackers can also access some plugin, core, or theme files directly. In that event, the server will not load the firewall to protect the site.
Once installed, it is possible to optimise the plugin. This involves the Wordfence plugin changing the PHP configuration to allow the firewall to load on the site before WordPress or any other PHP files that may be directly accessible. Depending on the configuration, this might involve changes to the .htaccess, .user.ini, or php.ini files. Once this process is complete, the plugin then provides Extended Protection.
As mentioned, Wordfence premium provides live updates of signatures to protect against the latest attacks. This version also provides a number of additional features, including:
Country blocking – This allows administrators to restrict access to the login page or the whole site to specific countries.
IP Blacklist – Administrators can choose to participate in the Wordfence Security Network, allowing the company to track malicious behaviour of specific IP addresses on a large number of sites. When an IP address is noted to be behaving badly, it is automatically added to the Wordfence IP Blacklist, blocking access to that IP address.
Defiant – Policies on Responsible Disclosure and Responsible Vendors
The most commonly used list of known vulnerabilities is the Common Vulnerabilities and Exposures (CVE) list which is maintained by the Mitre Corporation with the backing of the US Government. CVE Identifiers are assigned by a number of CVE Numbering Authorities (CNA).
As mentioned, the company behind the Wordfence plugin is Defiant Inc. The company regularly publishes research on its blog and podcasts. Vulnerabilities are always going to be present in computer systems and services. Finding them, disclosing those vulnerabilities responsibly and working to fix them is how the software developers and information security professionals work together to improve products and services and keep the public safe.
Defiant Inc uses a well-established process to disclose WordPress disclosures that is widely used by other organisations like Google’s “Project Zero” and Cisco’s “Talos” security team.
Using such processes can give the end-users confidence in the product, providing that the software vendors act on any disclosures in a timely manner and ensure that vulnerabilities are patched. There is also a degree of responsibility on the part of the end users to ensure they are installing patches as advised by the vendor.
The team at Defiant work closely with vendors to fix vulnerabilities and only disclose those vulnerabilities in a responsible way. When security researchers do not disclose vulnerabilities in a responsible way, this creates a big problem. If the owners of a project with a vulnerability are not given the opportunity to fix the issue and release a security patch before the disclosure is made, this inevitably leads to hackers exploiting these vulnerabilities (Wordfence, 2018).
On to Part 3 – OWASP – The Open Web Application Security Project
Back to Part 1 – Introduction, Methodology and Objectives